Inside ILProtector and Writing an Unpacker
The core protection principle of ILProtector is dynamic method. This article provides a detailed introduction to the protection details of ILProtector and specifically writes out the unpacker targeting it.
Introduction
ILProtector can be considered as an obfuscator with good compatibility and lacking strong protection capabilities. Although there is almost no information about this obfuscator online, there are unpackers released by CodeCracker and some unpackers improved based on his unpacker.
These unpackers have become invalid in the latest version of ILProtector, but the principles have not become invalid. Many people only use these unpackers without knowing the principles behind them. Once these unpackers become invalid, they will not be able to unpack the shell.
This article will explain the protection principle of ILProtector and write our own unpacker based on a project open-sourced on GitHub (ILProtectorUnpacker by RexProg).
Before the research, we still need to find a sample of ILProtector protected. Unfortunately, we did not find the latest UnpackMe of ILProtector protected online, so we directly use the main program of ILProtector (the website says “ILProtector is protected by itself!”).
During the research, version 2.0.22.4 of ILProtector was used, but when writing the article, it was discovered that ILProtector had been updated to version 2.0.22.5, which is a bit embarrassing. However, I have tested that there is no difference between version 2.0.22.5 and 2.0.22.4. Therefore, this article still uses the main program of ILProtector v2.0.22.4 as the sample for research. Here is the download link for the protected file: ILProtector v2.0.22.4.7z
Overview of ILProtector protection
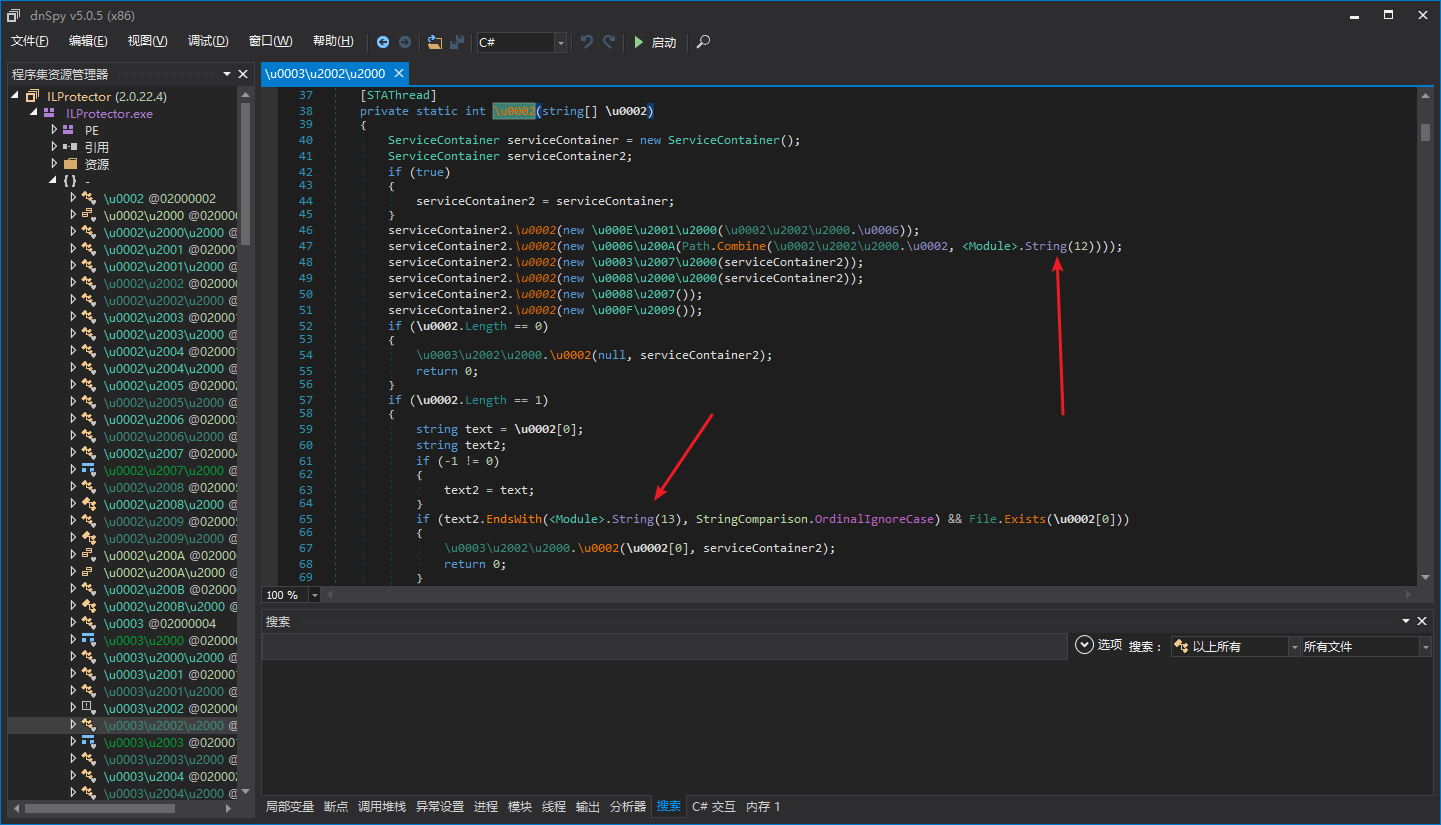
Let’s first open ILProtector with dnSpy to see how it is protected:
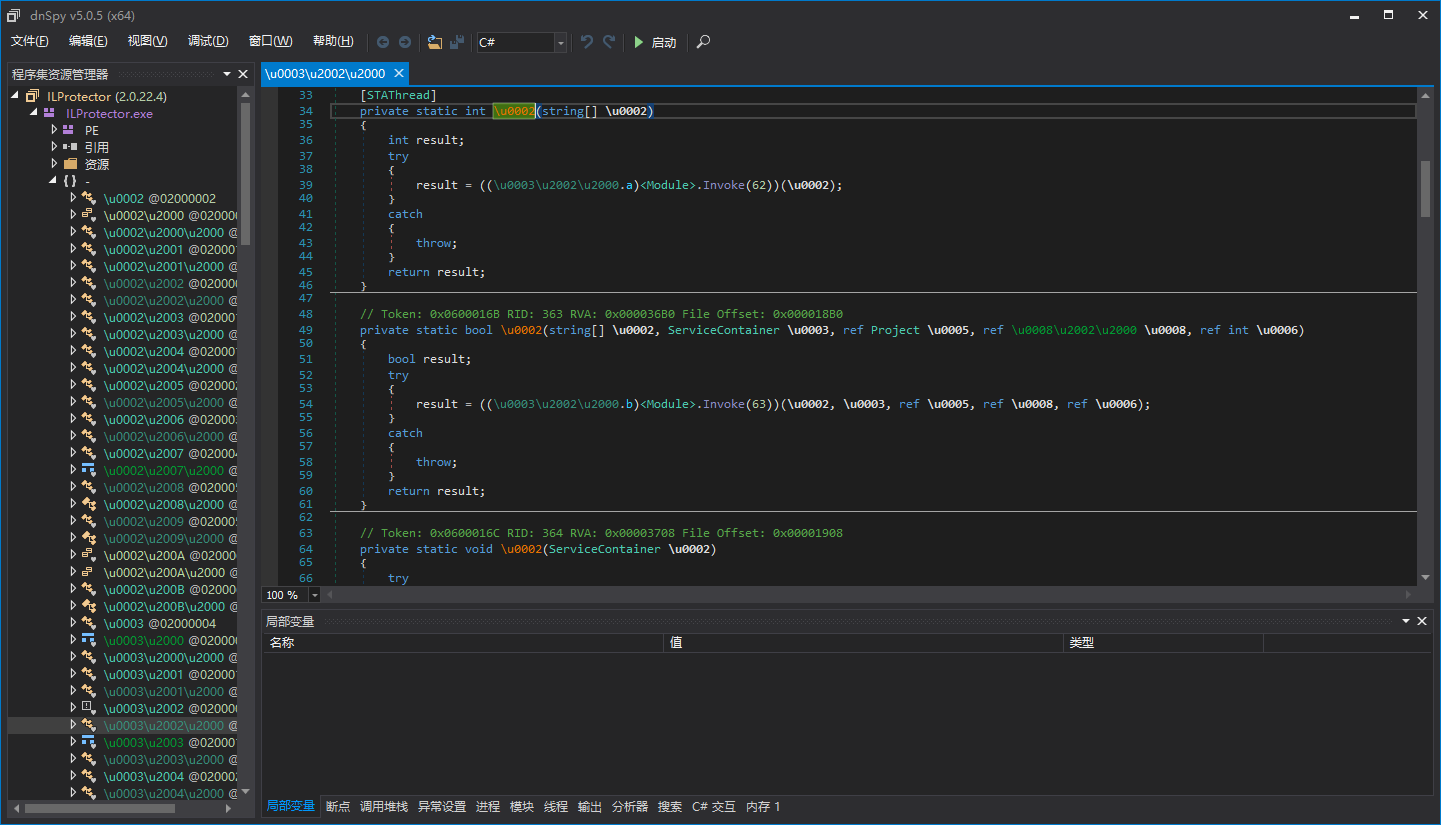
We can see that the method body has been hidden and replaced with “<Module>.Invoke(num)”. Let’s try to debug with dnSpy:
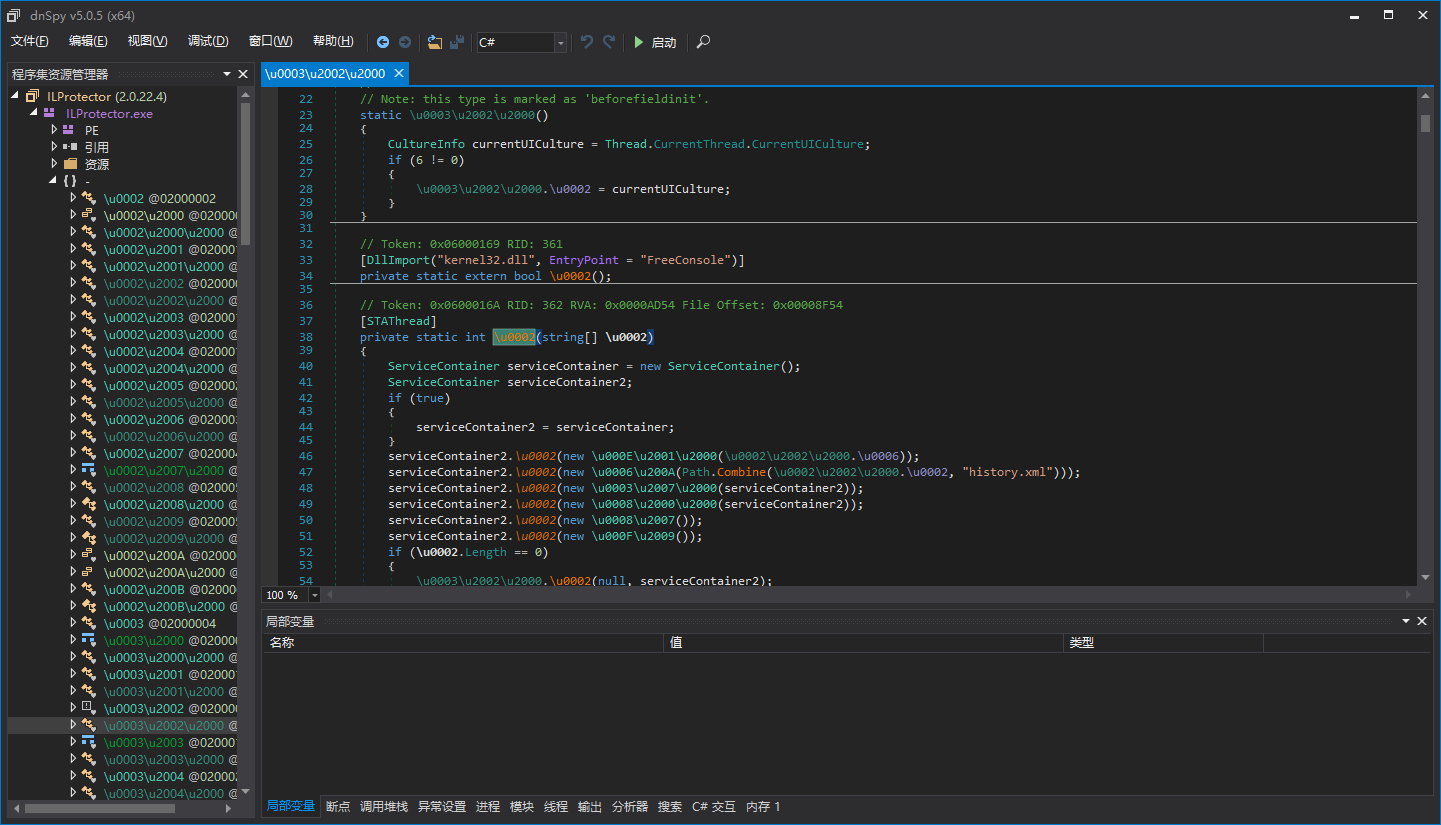
Set a breakpoint here at the Main method:
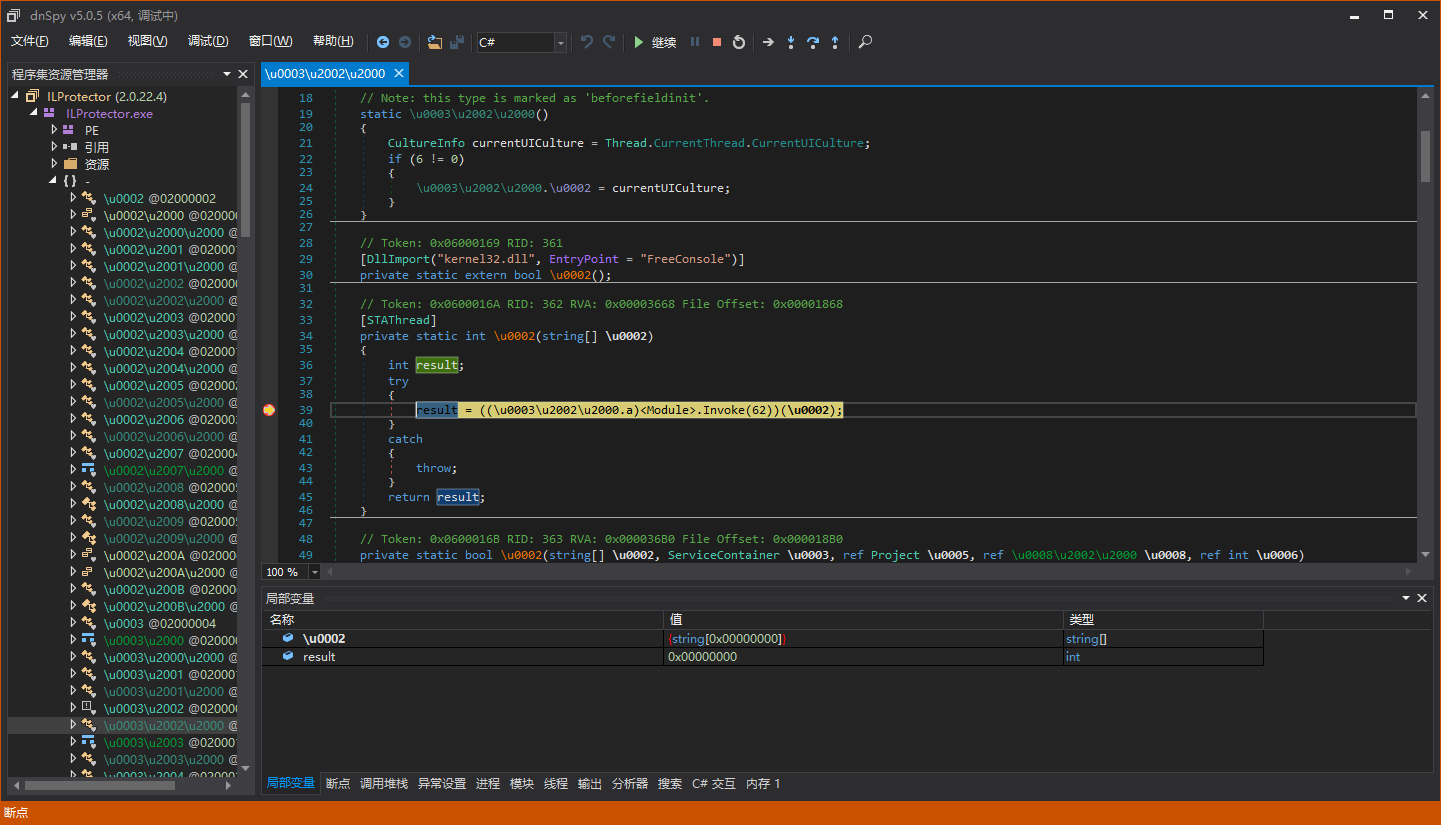
After breaking, step into the code with F11:
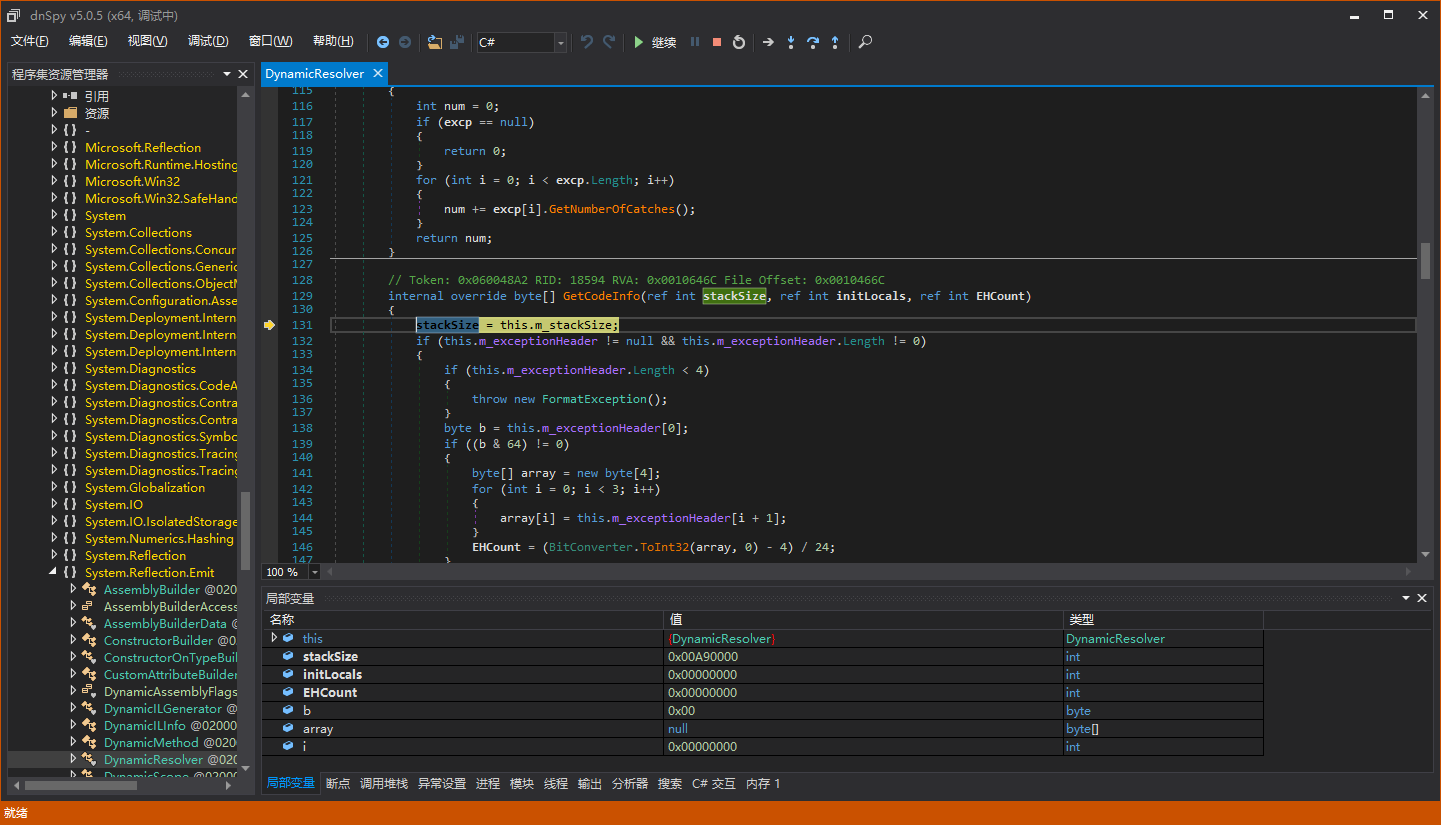
We can preliminarily judge that DynamicMethod was used. Let’s set a breakpoint at the constructor of DynamicMethod and run with F5:
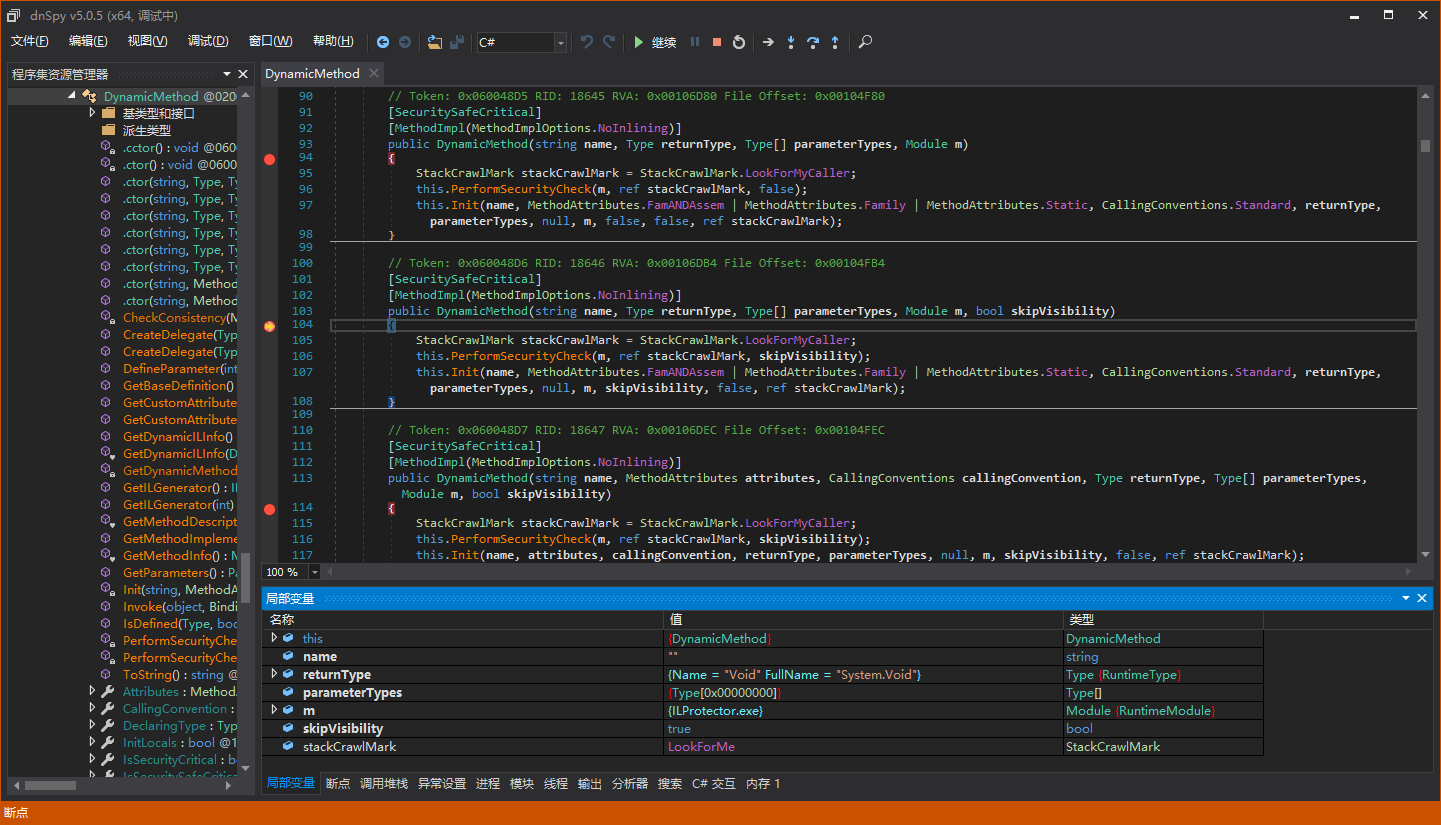
Yes, our guess was correct. ILProtector uses DynamicMethod to dynamically generate a method body to protect the assembly.
Unpacking principle of RexProg’s ILProtectorUnpacker
Unpacking process
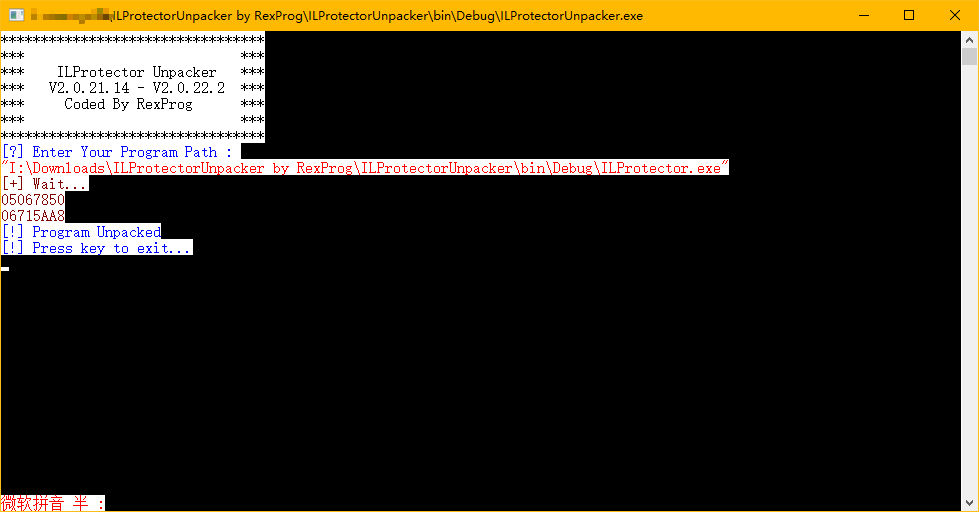
To avoid various attempts without significant meaning, let’s see how the mentioned open-source project achieves unpacking. Let’s first open this project in vs. (This provides a packaged project for download: ILProtectorUnpacker by RexProg.7z)
Find the Main method to see what’s going on (the following comments are added by myself):
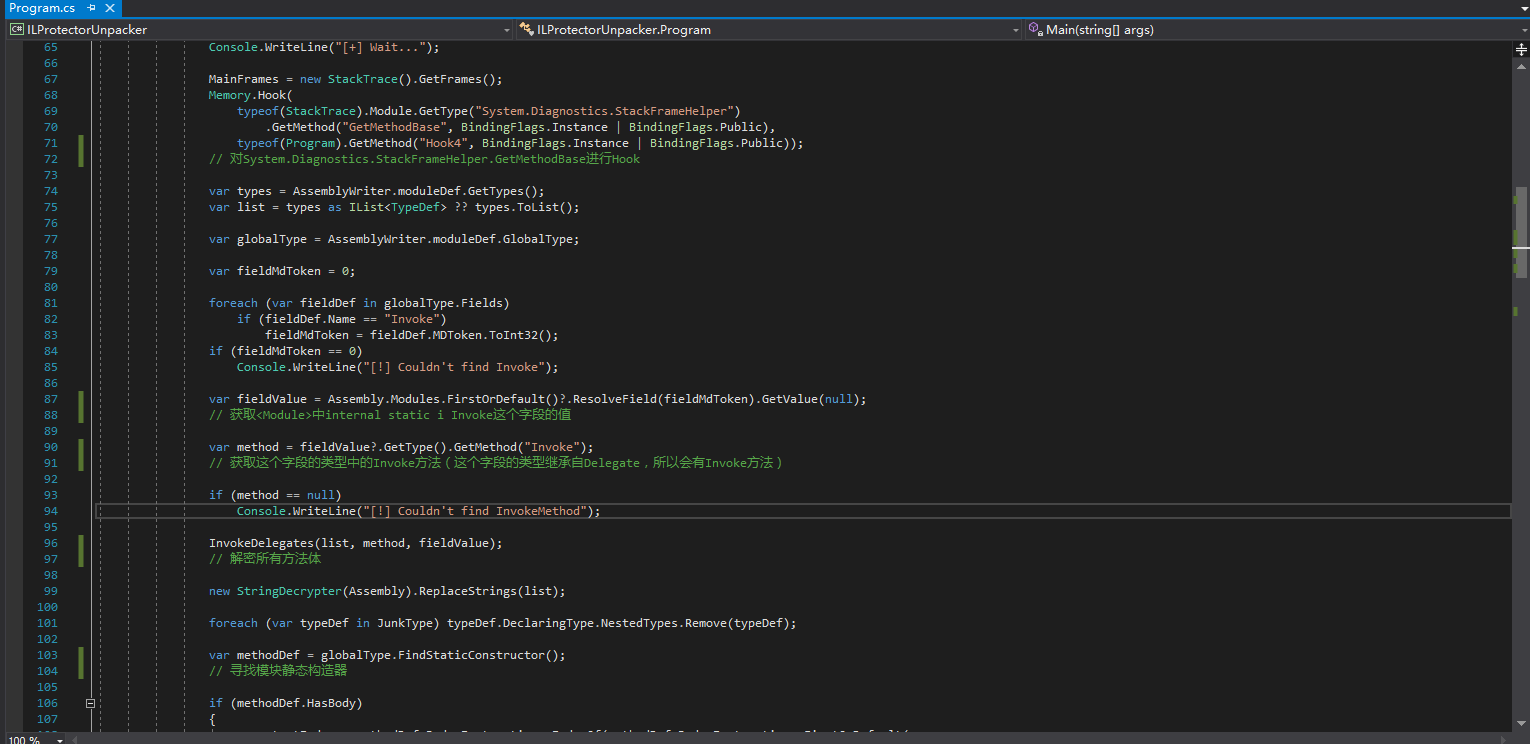
It can be seen that the actual implementation is in InvokeDelegates, so let’s go to this method:
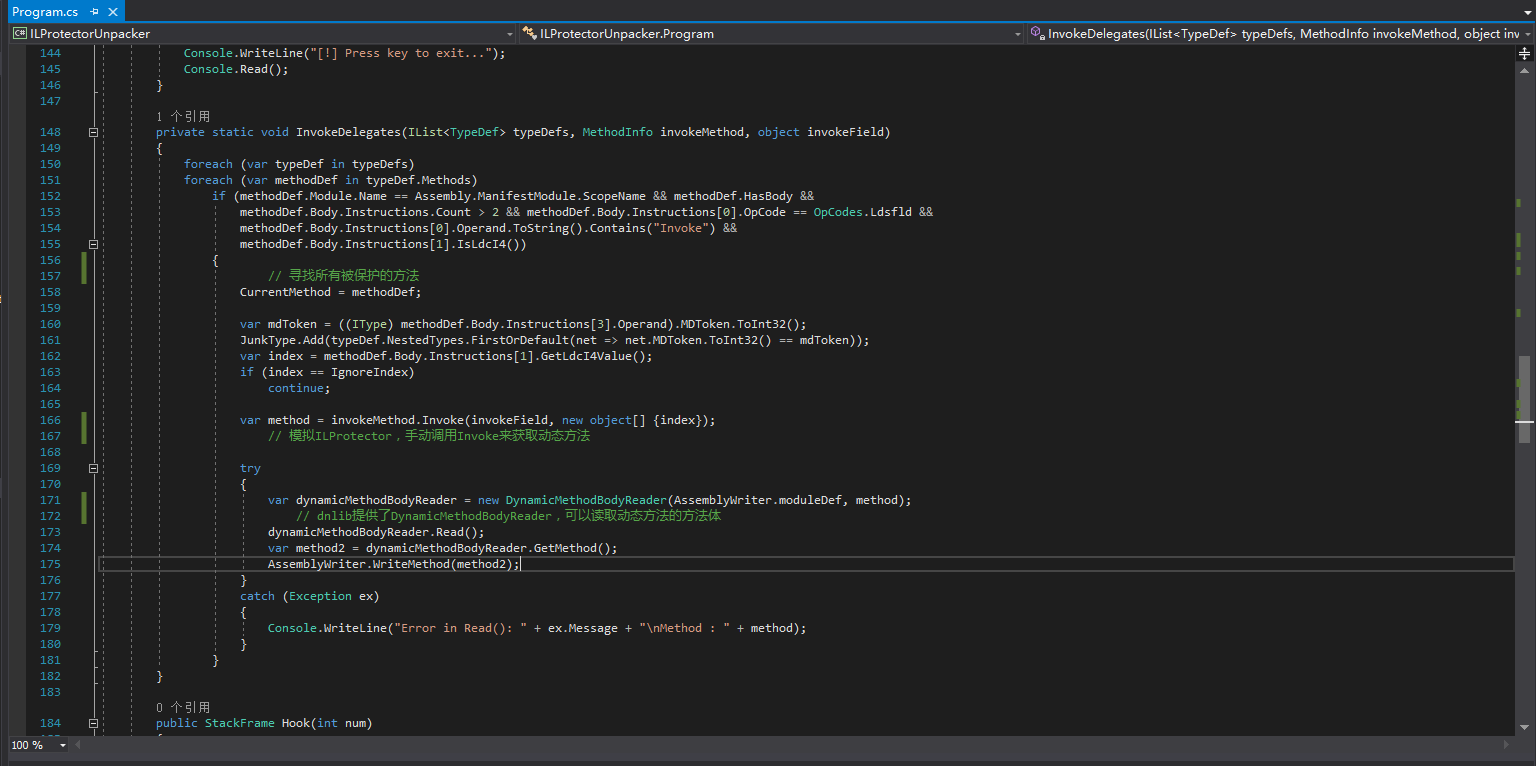
Bypassing detection
Now we have a basic understanding of the unpacking process. The unpacker first loads the protected assembly, then hooks a location, manually calls Invoke to obtain the dynamic method, and uses DynamicMethodBodyReader provided by dnlib to read the method body of this dynamic method and restore it to the method body in the file. We mentioned earlier that since it is a hook, it is most likely related to bypassing detection measures. Let’s see what was hooked:
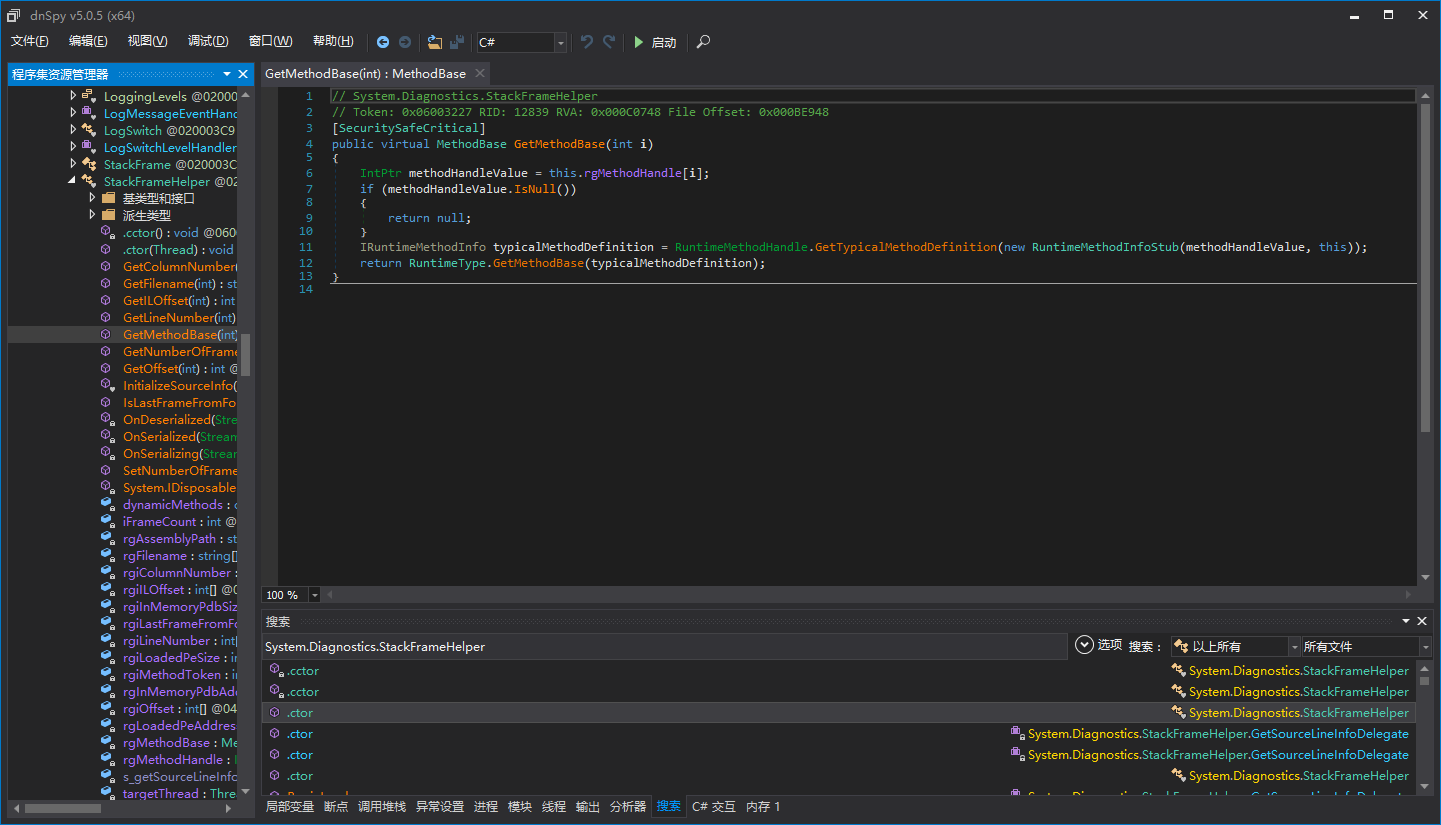
The corresponding detour:
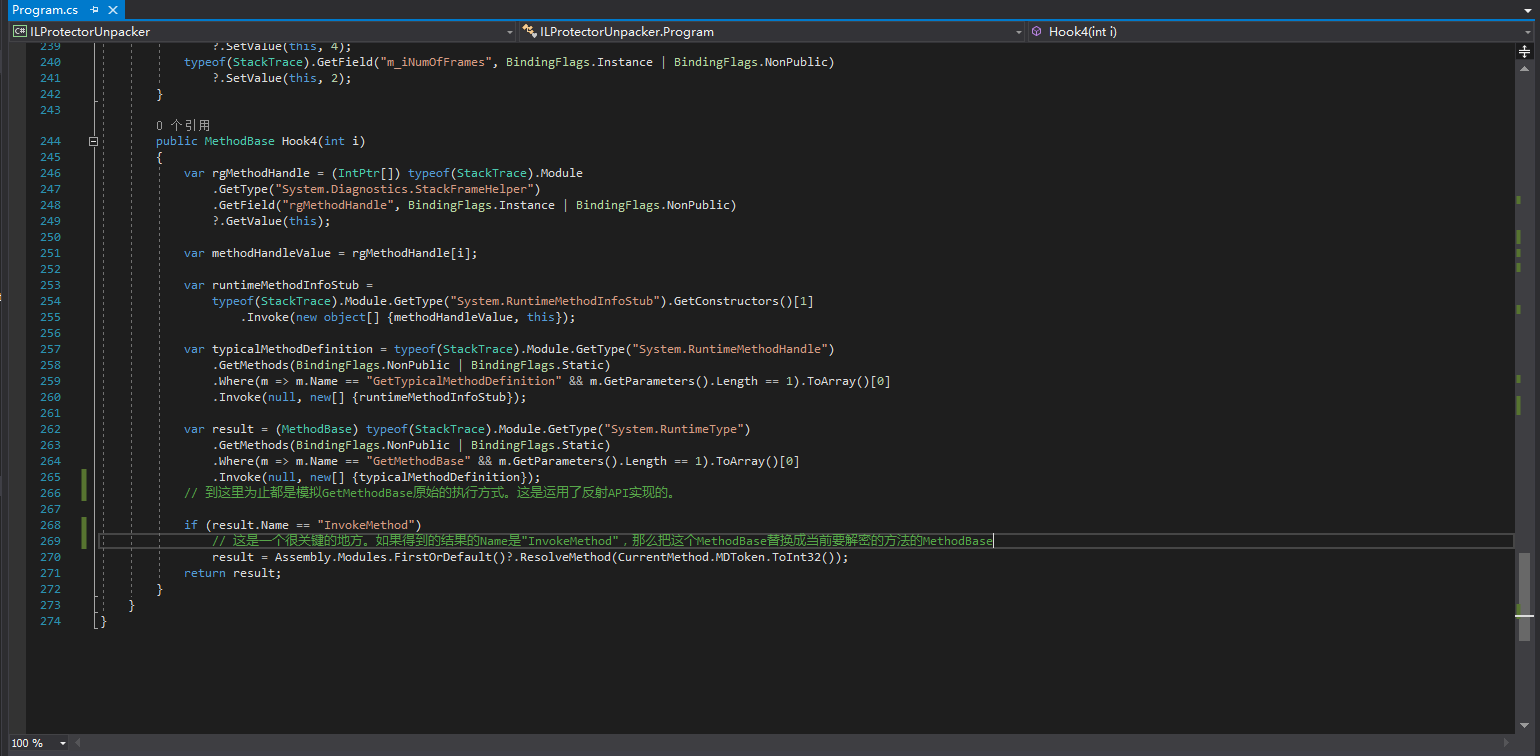
At this point, we are not quite sure why System.Diagnostics.StackFrameHelper.GetMethodBase needs to be hooked, nor do we understand what InvokeMethod means in “if (result.Name == “InvokeMethod”)”. Let’s search for InvokeMethod again with dnSpy and decompile it:
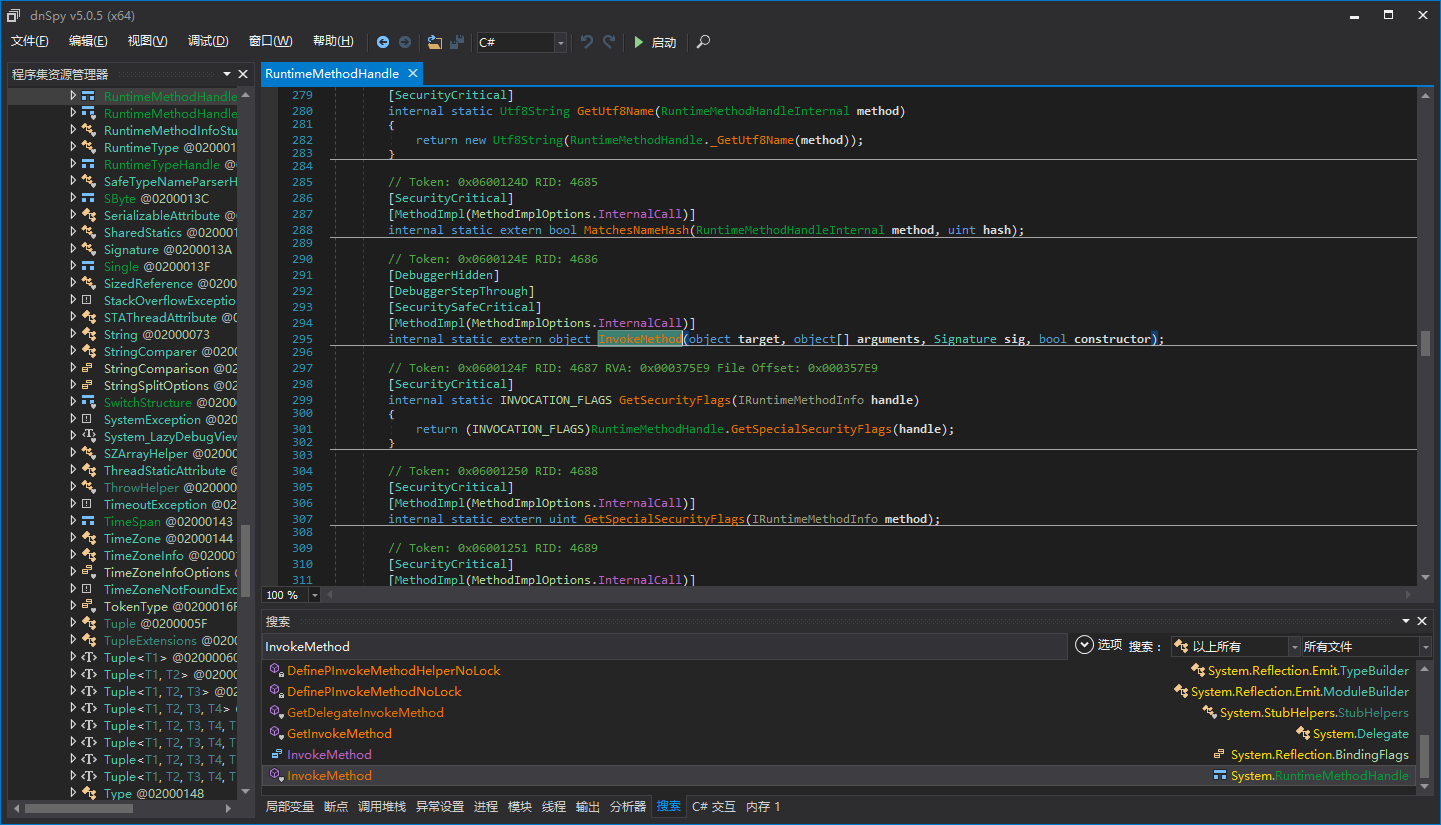
For those with some reverse engineering experience, they should know that this is where the CLR enters from managed code when calling MethodInfo.Invoke, similar to R3 transitioning to R0 in Win32 programming.
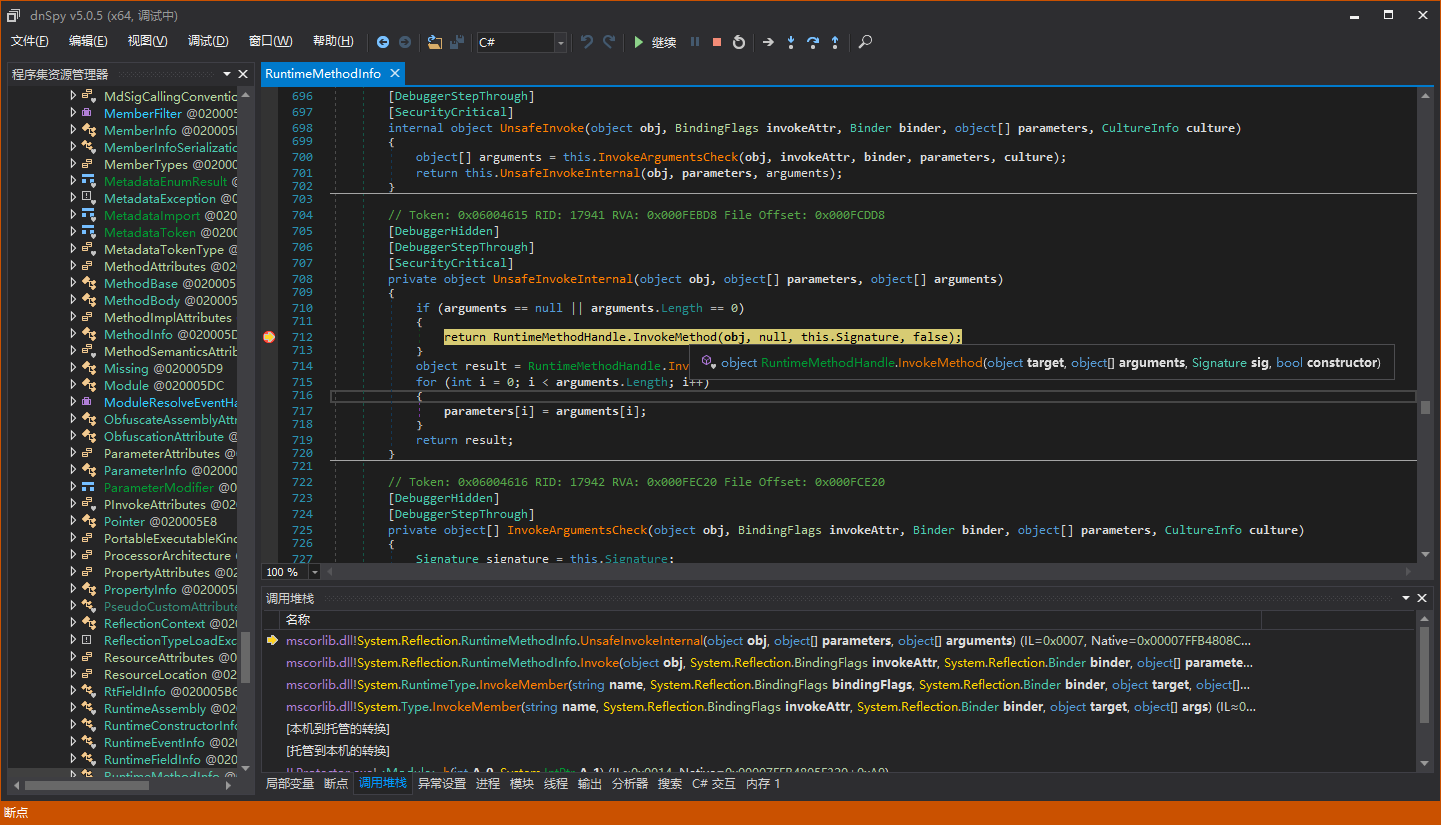
Combining with some principles of detecting illegal calls, we can know that ILProtector will check the previous method in the call stack of the protected method. For example:
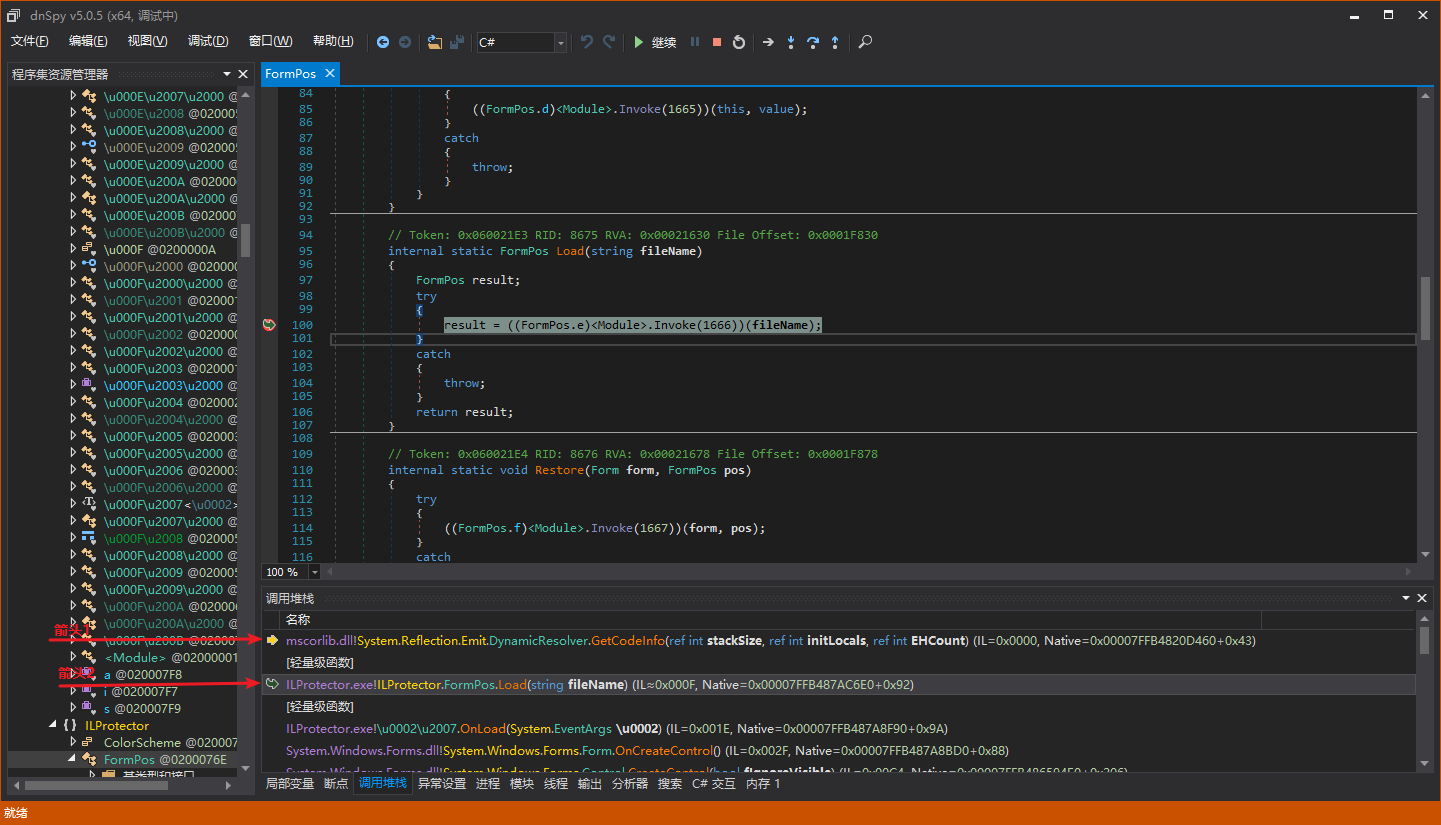
Suppose the arrow 2 points to the protected method, and arrow 1 points to the non-managed code running with ILProtector (treat it as such, because dnSpy cannot step into non-managed code). Then the non-managed code at runtime will check whether the caller pointed to by arrow 2 is the protected method, i.e., “internal static FormPos Load(string fileName)” here. If we manually use Invoke to obtain the dynamic method, the non-managed code detected will not be “internal static FormPos Load(string fileName)”, but “System.RuntimeMethodHandle.InvokeMethod” mentioned earlier. Therefore, RegProg’s unpacker hooked GetMethodBase and wrote
1 | if (result.Name == "InvokeMethod") |
to bypass detection.
This explanation may be a bit difficult to understand, although it has been explained in as much detail as possible. Readers may not fully grasp it, but they have a general idea. Therefore, it is still necessary to debug and trace it by yourself to truly learn the knowledge through practice!
An error occurred!
Looking at what I wrote, don’t you think that ILProtectorUnpacker is written perfectly? However, the higher the level, the tougher the opponents, so there will be anti-detection measures even with anti-detection measures. Let’s compile and run RexProg’s unpacker directly:
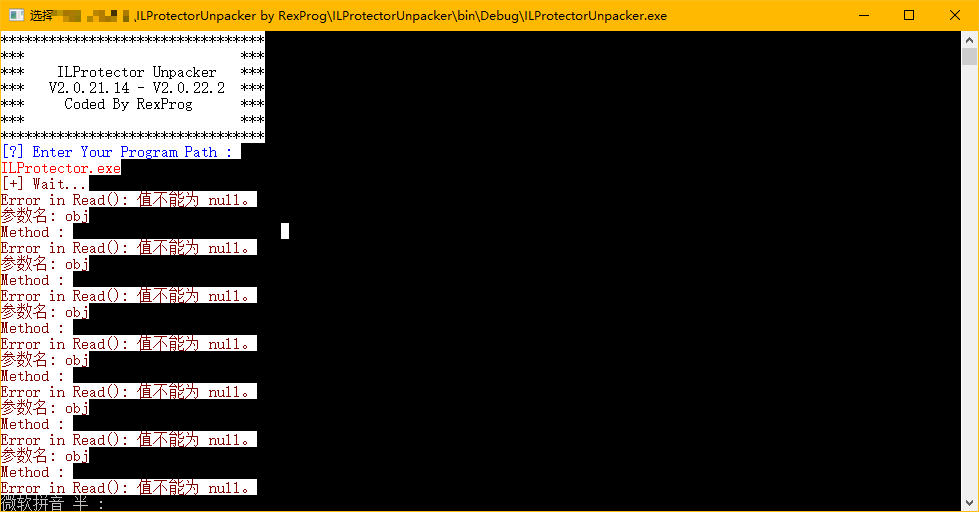
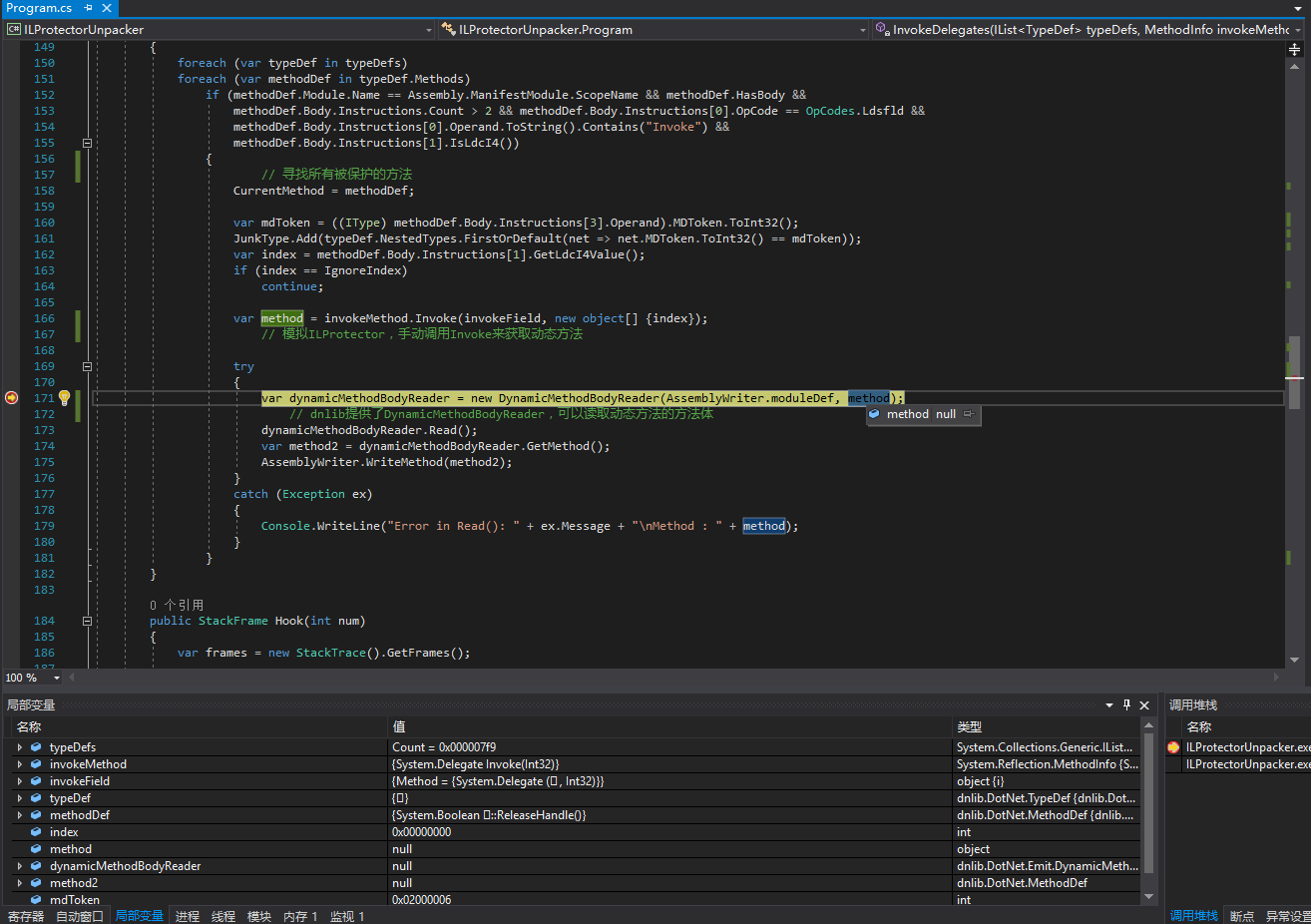
Why did this happen? After various analysis and attempts, and for the sake of simplicity, the correct process of analyzing and detecting anti-detection measures (ILProtector detected that we manually called Invoke) will be directly written here.
ILProtector’s detection
First, ILProtector checks the call stack. We have handled it and it works normally, so why would ILProtector still detect illegal calls? The answer is that ILProtector detected our hook.
Modify Memory.Hook to output some information (the address of target and detour in hook):
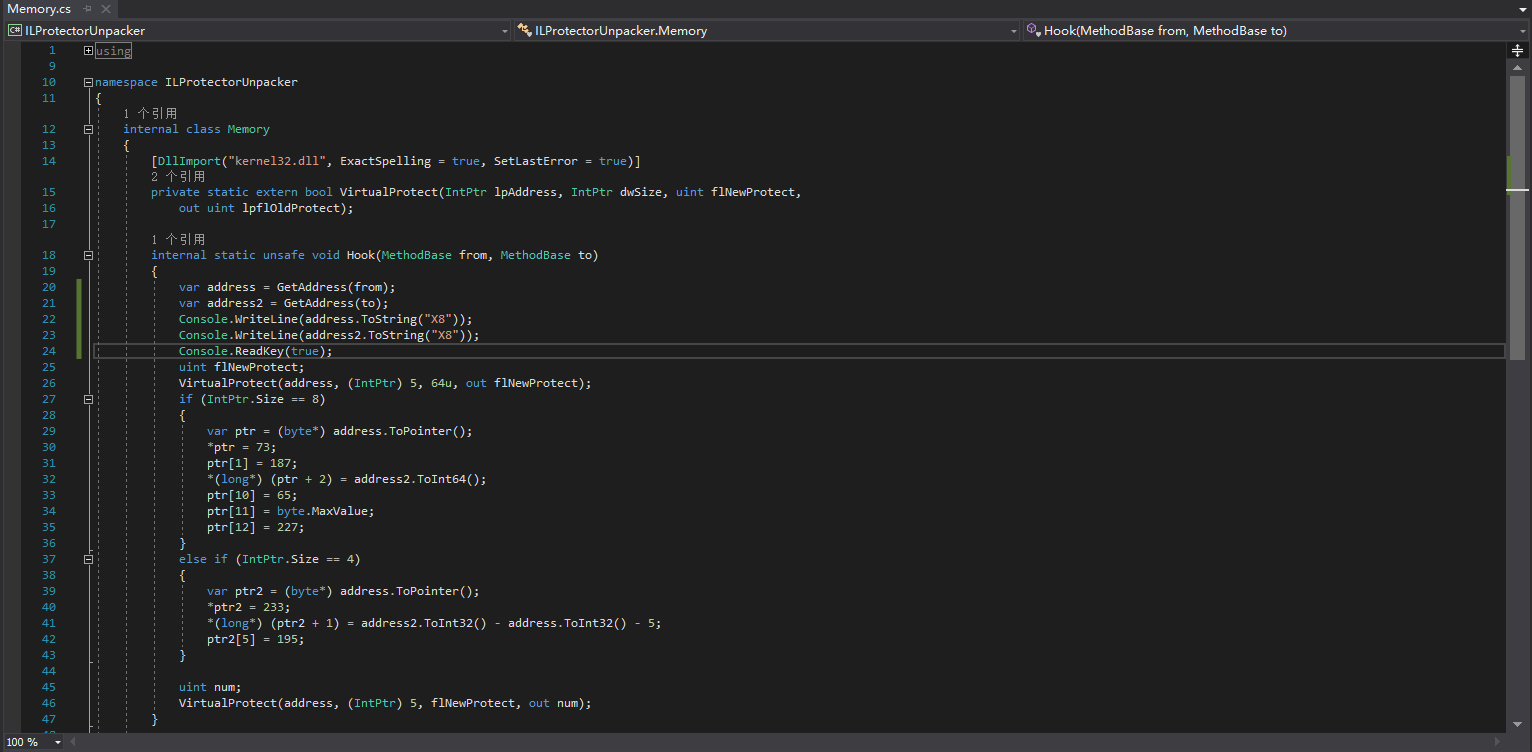
Open x64dbg, start the unpacker, and let the unpacker run until it stops at “Console.ReadKey(true);”:
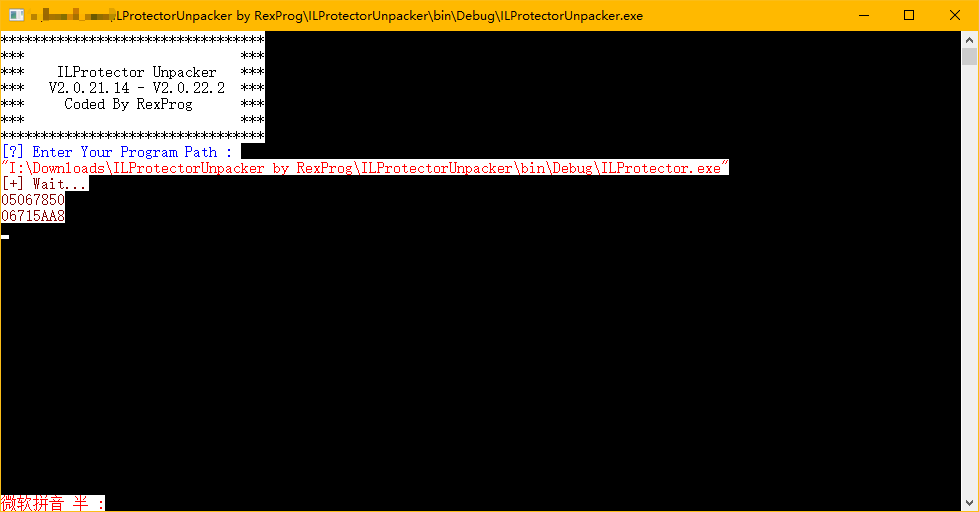
In the memory window of x64dbg, go to the first address. The first address is the address of the method being hooked, i.e., the address of System.Diagnostics.StackFrameHelper.GetMethodBase. Then set a hardware access breakpoint for System.Diagnostics.StackFrameHelper.GetMethodBase:
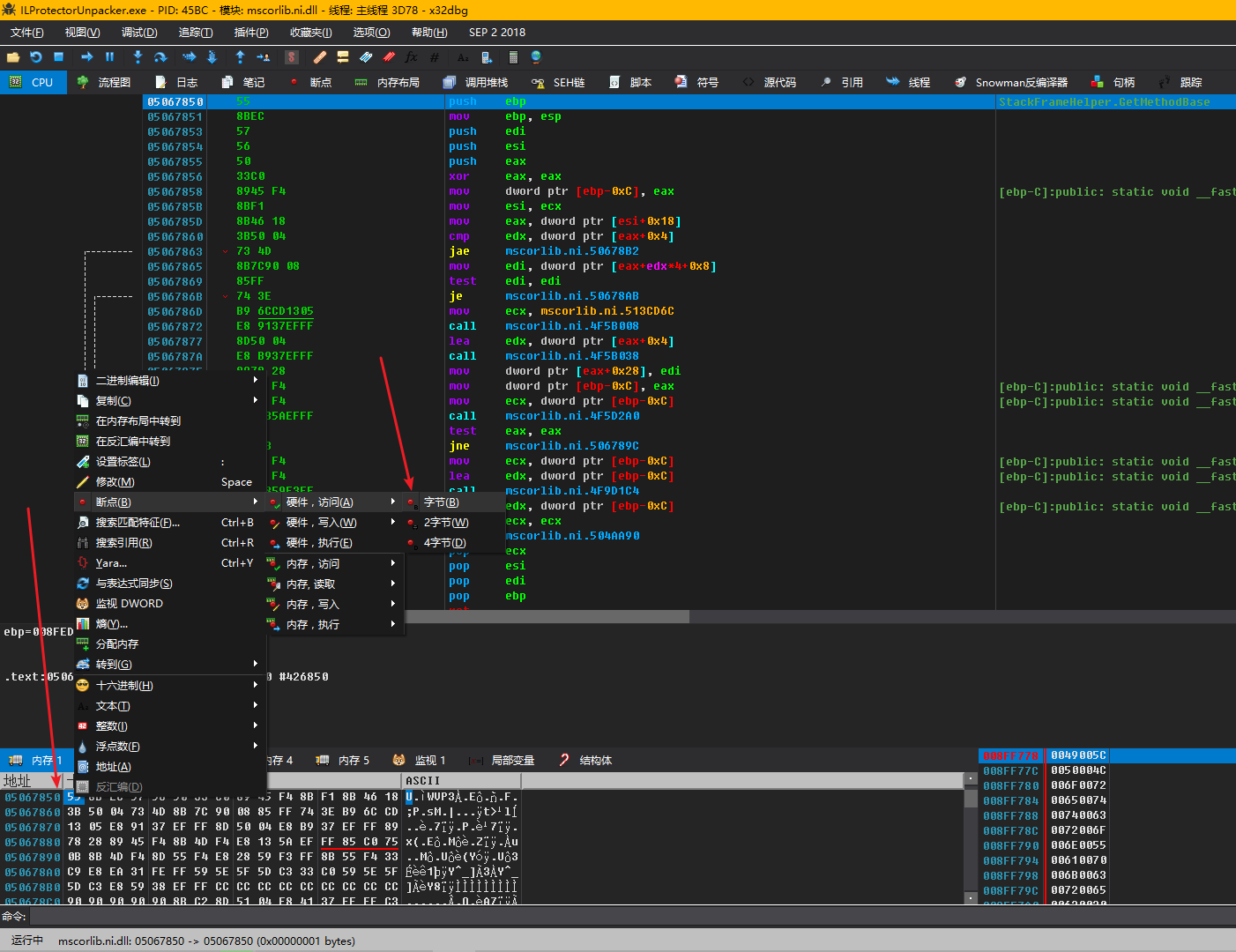
Press any key in the console to let the unpacker continue to execute until it breaks at ProtectXXX.dll.
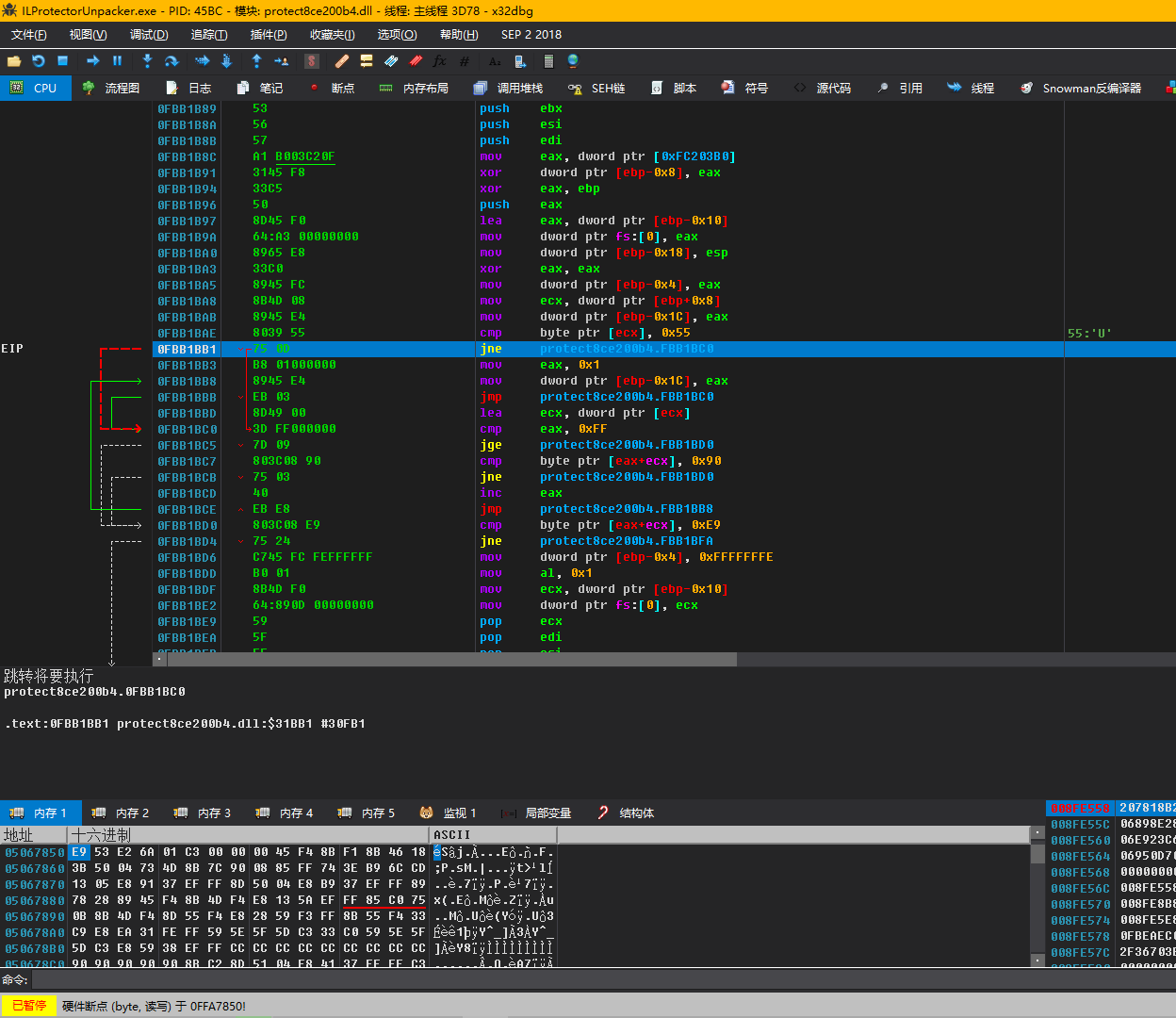
This is a jcc instruction, which further proves that this is checking whether it is being Hooked. For convenience, and because this is an unencrypted DLL, we can just use IDA to decompile this hook detection function. The RVA of this function is 0x31B70, so just search for “31B70” in IDA.
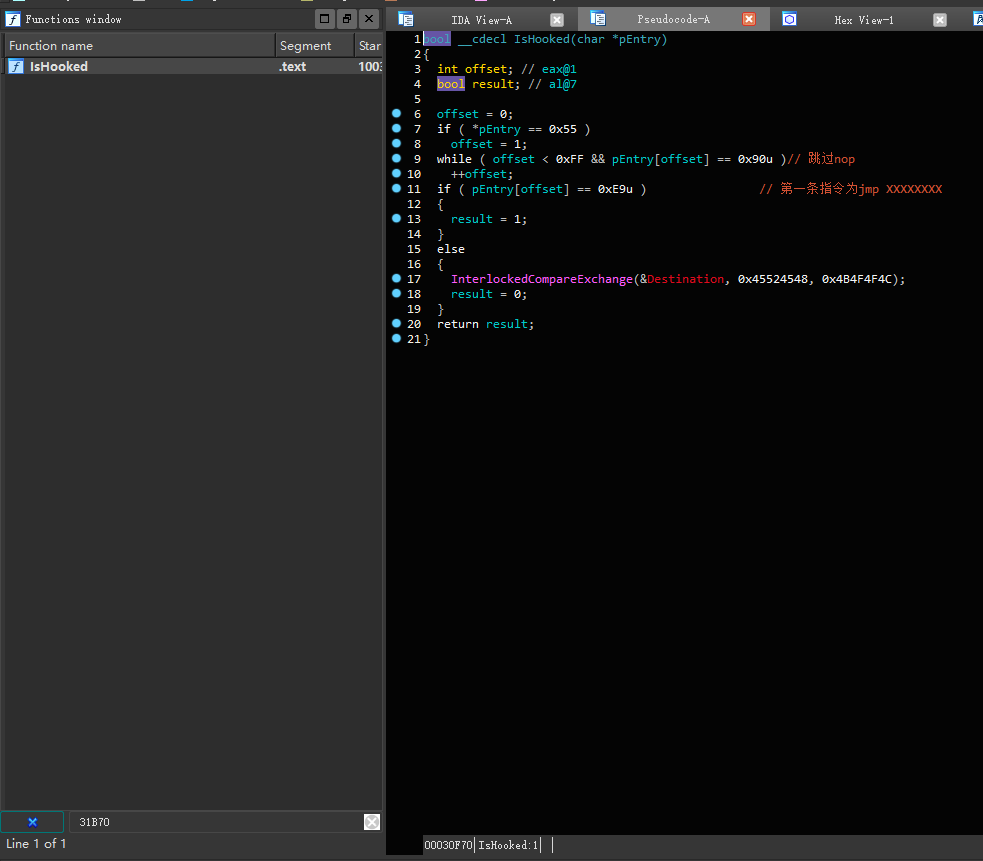
I have already renamed the code, so readers can directly think about the principle of this detection. I will briefly explain this detection:
IsHooked(char *pEntry) is passed in the address to be checked, such as 0x05067850 this time using x64dbg for debugging.
1 | if ( *pEntry == 0x55 ) |
This code can be considered garbage code and does not need to be understood.
1 | while ( offset < 0xFF && pEntry[offset] == 0x90u )// Skip nop |
Skip nop.
1 | if ( pEntry[offset] == 0xE9u ) // The first instruction is jmp XXXXXXXX |
Check whether the first instruction after the nop (if there is one) is jmp. If it is jmp, return true, indicating that the hook has been detected; if it is not jmp, it means that the code is normal and has not been Hooked. Set a flag (this flag does not matter) and return false.
Bypassing ILProtector detection again
Don’t forget that we have countless ways to write junk code and directly bypass the detection.
Let’s first see what the unpacker changed System.Diagnostics.StackFrameHelper.GetMethodBase into:
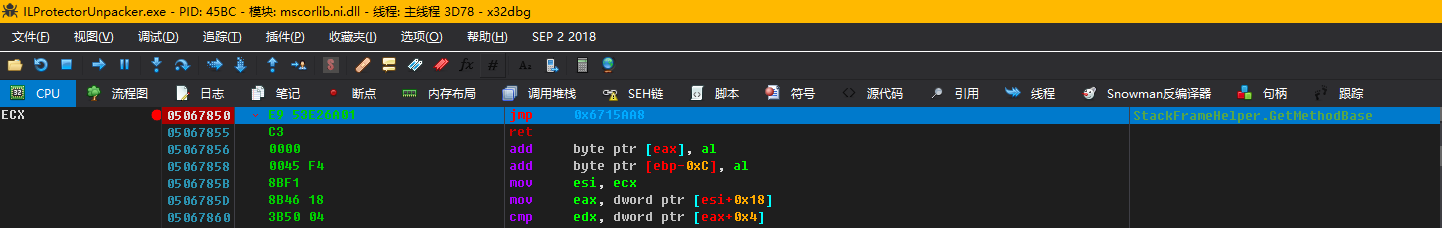
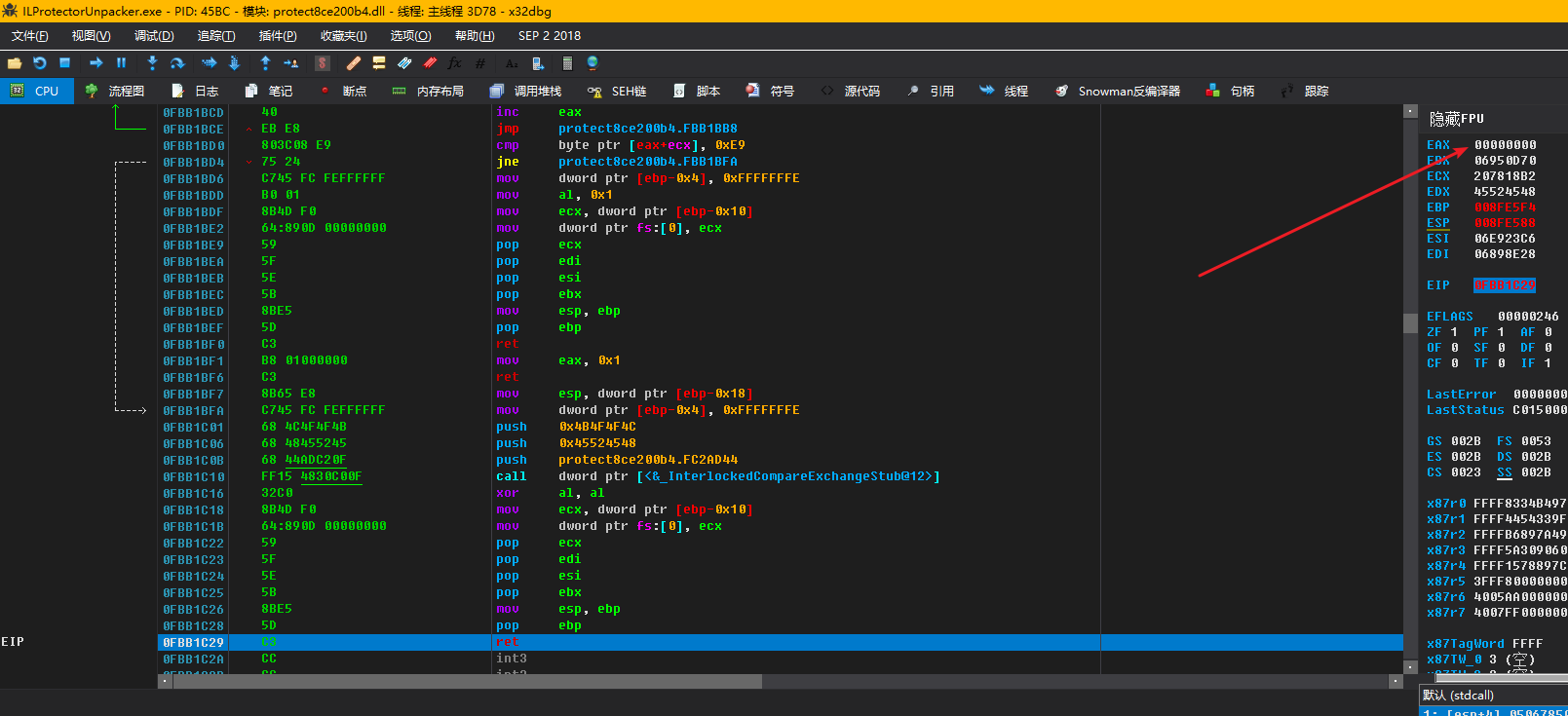
No wonder it was detected. The first instruction is jmp, and the hook is too obvious. Let’s do something fancy and add 0xEB 0x00 in front of “jmp 0x06715AA8”, which is equivalent to “jmp eip/rip+2”.
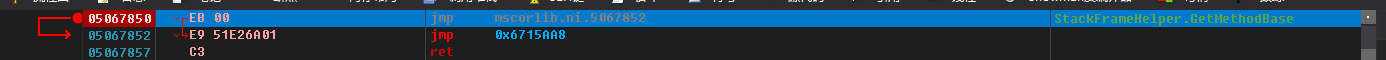
Step through until the hook detection returns with F8, and you can see that it returns false. Press F5 and find that the unpacker does not report an error, which means our passing of the detection was successful!
Our own unpacker
So the research on RexProg’s ILProtectorUnpacker and on ILProtector itself can come to an end. Next, let’s explain how to write our own unpacker.
Let’s start with a simple framework:
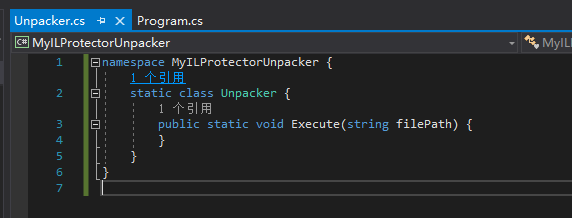
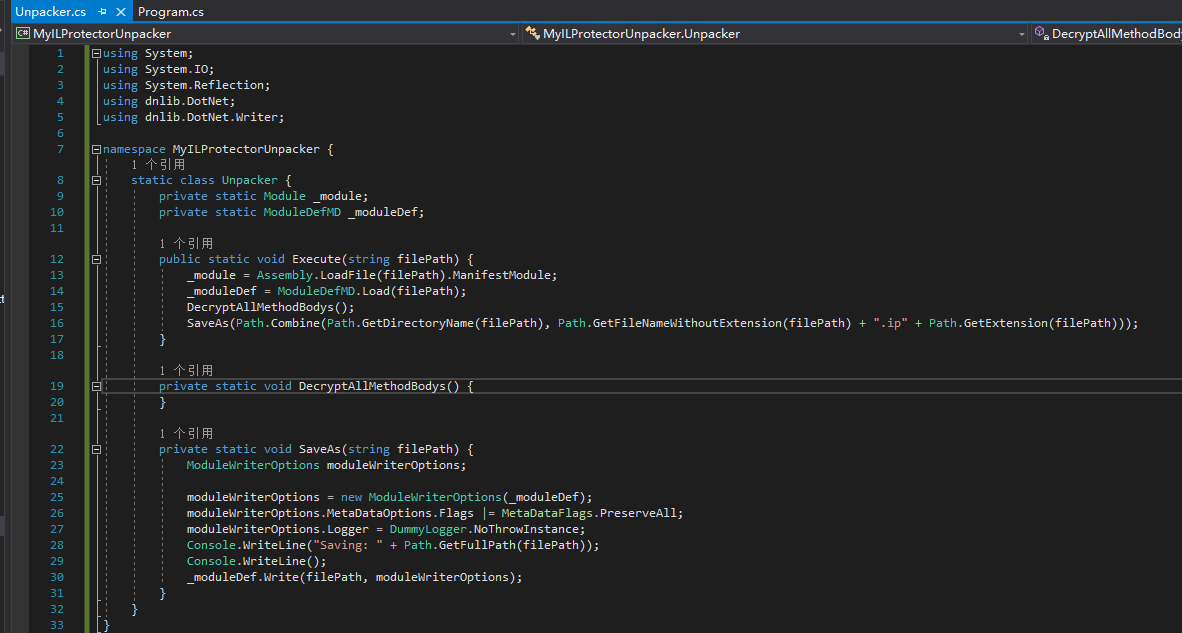
Before calling DecryptAllMethodBodys, we need to hook System.Diagnostics.StackFrameHelper.GetMethodBase.
GetMethodBase is an instance method, so we will create a class specifically for placing the detour method, and insert reflection API initialization code in the static constructor of this class:
1 | Module mscorlib; |
Note that because it has been Hooked, the “this” pointer is incorrect, and fields such as FieldInfo_rgMethodHandle should be defined as static fields. If you don’t understand, you can change it to non-static and see what error occurs. We won’t demonstrate it here.
Compared to using GetMethodByName directly, I prefer to use Attributes to retrieve my detour. Let’s define a DetourAttribute:
1 | private sealed class GetMethodBaseDetourAttribute : Attribute { |
Back to the class where the detour is placed, write this code:
1 | [] |
Now we can use
1 | private static MethodInfo GetMethodByAttribute<TClass, TMethodAttribute>() where TMethodAttribute : Attribute { |
to get the detour without worrying about when the code is obfuscated and GetMethodByName fails.
1 | private static void* GetMethodAddress(MethodBase methodBase) { |
With this method written, we’ll write another new method to get the address of target and detour, first write junk code to tagret, and then write the actual jmp.
At this point, we can add the following to Execute(string filePath):
1 | if (Environment.Version.Major == 2) |
Next, let’s write the previously defined DecryptAllMethodBodys(). First, define variables inside the method:
1 | TypeDef globalType; |
Then, we need to use reflection to get “internal static i Invoke” in <Module>. methodTableLength represents the total number of methods in the assembly, so we will iterate through each method using a for loop to implement it:
1 | globalType = _moduleDef.GlobalType; |
methodTableLength represents the total number of methods in the assembly, so we will iterate through each method using a for loop to implement.
1 | for (uint rid = 1; rid <= methodTableLength; rid++) { |
Define variables inside the loop body:
1 | MethodDef methodDef; |
methodDef represents the current method being resolved, and dynamicMethod represents the value returned by i.Invoke(num), which is a delegate. The delegate’s internal code is a dynamic method.
1 | methodDef = _moduleDef.ResolveMethod(rid); |
At this point, we are ready to Invoke and restore, so we’ll add them.
1 | try { |
When we run the unpacker, we can see that the method body can really be decrypted. If you truly write an unpacker from scratch, it is truly exciting and rewarding to have achieved results through research on your own, isn’t it?
But we can see that there seem to be some strings that have not been decrypted. Let’s revisit “internal static s String” in <Module>. This is similar to Invoke - the same way to call it can decrypt strings. We won’t paste the code here because it’s really the same, and it’s not checked, so just call it directly.
The effect of decrypting strings:
Next, we need to remove the initialization code of ILProtector at runtime. Although it doesn’t matter if it’s not removed, for the sake of perfection, let’s improve the unpacker:
1 | private static void RemoveRuntimeInitializer() { |
The variable startIndex in the code represents the beginning of the runtime initialization code, and endIndex represents the code immediately following the end of the runtime initialization code. Due to the possibility of jumps within the method body and some features of dnlib, we cannot simply replace the Instruction with Nop, but must do it like this:
1 | instructionList[i].OpCode = OpCodes.Nop; |
In addition to this, there may be other residual code caused by ILProtector in the protected assembly, and we will not elaborate on the removal methods one by one.
There is not much point in releasing a finished unpacker. It is still hoped that readers can study and develop their own unpackers based on the article. Instead of just using someone else’s unpacker, which will become ineffective if the packer tool is updated someday.
Inside ILProtector and Writing an Unpacker
https://wwh1004.com/en/inside-ilprotector-and-writing-an-unpacker/